10 Nov 2022
This was originally posted on Reddit here.
I passed the OSCP 6 weeks ago and wanted to provide the obligatory Reddit post explaining how I went about it and more importantly I wanted to wait to test out the value of the certificate itself in the jobs market. I would also like to say that this is all anecdotal and just my experience so any advice or recommendations may not work for everyone so take from this the bits you think might be useful.
Background
I have 15 years in Investment Banking IT but none of it was Cyber Security related. I started as a Java Developer and eventually onto Management. On that journey I would have needed to build SQL queries from time to time so I had that plus some basic Linux knowledge.
Preparation
I started preparing at the beginning of the year. I started off by doing the following paths on THM although I only partially did the Jr one to fill in any gaps from the previous 3:
- Complete Beginner
- Web Fundamentals
- Offensive Pentesting
- Jr Penetration Tester
After that I started working through TJ Null’s list on PG Practice/Play which is a great resource and I completed them all. I did all of the above over 6 months whilst working full time then I took a career break for 6 months to focus on the PWK itself. Obviously, everyone wouldn’t have this luxury but I had a bit of savings to allow me to do it.
PWK
I joined the PWK when it was still the old pdf that you submitted so I spent probably a month full time working on that which wasn’t a pleasant experience to be honest and felt like a real grind. After that I spent the 2nd month of my 3 months PWK working in the labs.
As others have said a lot of the boxes use old exploits so there were times I got root not knowing for sure if it was the intended way which was frustrating. I also experienced times when pivot boxes would get reset when I was trying to hack the internal networks undoing all the setup I had in place which is no fault of Offsec just life.
I think the real shame in regards the labs is that the former exam machines are in an internal network. They are the jewel in the crown of the labs where we can actually test ourselves against what Offsec think is an exam worthy box but because they are put internally the exploit that would have worked on the original exam may not work now without some sort of customisation. I think moving the 5 former exam machines to the public network would increase the value of the labs immeasurable overnight. The AD sets in the labs and in the ‘Topic Exercises’ are a great resource though so do them.
After doing about 30 boxes in the labs I left with a month remaining on my time and went seeking out Windows boxes. As we all know this is predominantly a Windows exam now (which I will discuss further later) so I did the Windows boxes on HTB from TJ Nulls list. I spent the next 2 months working through some AD and all of the Windows boxes on his list and also on Cyber Sec Labs which is a great site too. In the last month I was no longer trying to get admin as quickly as possible but seeking out boxes to test areas where I was weak which is what you should do too.
As someone said you don’t really know if you are ready for the exam but it just got to the stage that I was sick of thinking about it to be honest so I booked it for late Sept so 9 months after I started prep.
Exam
Just before the exam I asked for a test proctor session which I was glad I got as I thought the Chrome webcam plugin would be run from Kali but it is actually run from Chrome on your host Windows machine. When I learned that it all worked fine although the memory use was relatively high even for me with 40GB of RAM. I’m glad I did it before exam day. I also had my Libre Office template supplied by Offsec ready for the exam.
I started the exam at 10am and went straight for the AD set which I advise everyone to do. I got in a lot easier than I thought I would. I can’t remember all the timings now but I think by 6pm I had cracked the AD set with domain admin privileges but I had one nagging doubt. Although the AD set is worth 40pts I wasn’t sure if that means there were 4 x 10 point flags or if there should be 2 flags per machine in the 3 machine AD set so 6 flags in total. Even reading the exam FAQ / Guide today it isn’t very obvious but I did read at one point that not all machines will have both flags but with exam stress I maybe forgot this.
Anyway I had 4 flags incl domain admin but I then went hunting for a flag that turned out not to be there which was stressful so that is a lesson to be learned for others taking the exam. I know I know with domain admin it should be easy to go anywhere but it wasn’t for me in a particular case plus exam stress.
I then moved onto the Buffer Overflow box and although I was able to do them in 20 mins on THM and it was very similar it took me a lot longer. I think mainly due to having to screenshot every step of Immunity Debugger like when removing characters etc. I think the shell coming back from that box was the biggest relief of the day so close to midnight. I was really tired at that stage and the effort to screenshot the whole process which if I had not got it working I’d have to redo would have been soul destroying. I then Priv Esc’d very quick and started making sure my days work all looked okay in my Libre office doc. It was now 2am so I finished up with 70 points that night.
I then tried to sleep but couldn’t until 4am and then woke again at 6am so went back to my office and got into 1 of the standalones which got me 80 pts plus 10 for the report so 90 overall.
It took me days to recover from the lack of sleep but within 24 hours I had been informed I had passed which was a great relief.
That was late September and after a week off I started the CRTP (which is an amazing course which I passed) and applying for jobs. All of a sudden with the OSCP on my CV/Resume firms started to take notice and I got offered a role as a Pen Tester today 6 weeks after passing the exam which illustrates how useful the OSCP can be. For that quick job success alone it was worth all the effort.
Tips
This is now mainly a Windows exam so spend most of your time working on Windows Priv Esc and AD. I spent the last month only doing Windows\AD boxes. In the exam I didn’t do any Linux hacking whatsoever and passed. If you get the BoF you can do that too or even without BoF it could be possible depending on the set. Obviously master the Linux stuff early on but near the end focus on Windows.
Software recommendations:
Use a VM so you can rollback. Installing Libre Office, Wine and many tools throughout the year broke my Kali build especially before I discovered virtual envs. Daily snapshots are your friend and I have mine set to snapshot on exit.
Autorecon is amazing which is what I used for my scanning. The odd time if something seemed strange I may follow up with Feroxbuster but I mainly used Autorecon. The key is to go into the Autorecon folder and start a webserver so you can work through the results in Chrome.
Terminator is a great emulator to use and I customized it to have my IP before the prompt and since Autorecon creates a folder with the target IP which I ‘cd’ into and worked from there I then had both the attacker & victim IP always easily available in my prompt area so pasting into reverse shell scripts etc is less hassle. I also set it so when I highlighted a piece of text it auto copied it which I recommend.
Webserver I used is called ‘Updog’ which is great for starting a webserver quickly.
I think PrivEscCheck is probably a tad better for the current exam than WinPeas and I also did use Bloodhound which helped me to understand a path I should be looking for.
Joplin with the tabs plugin is the ultimate note taking tool for me. Here is a screenshot of my notes layout. Across the top are the tabs of everything I needed then each tab when clicked allows you to add notes down the vertical side.
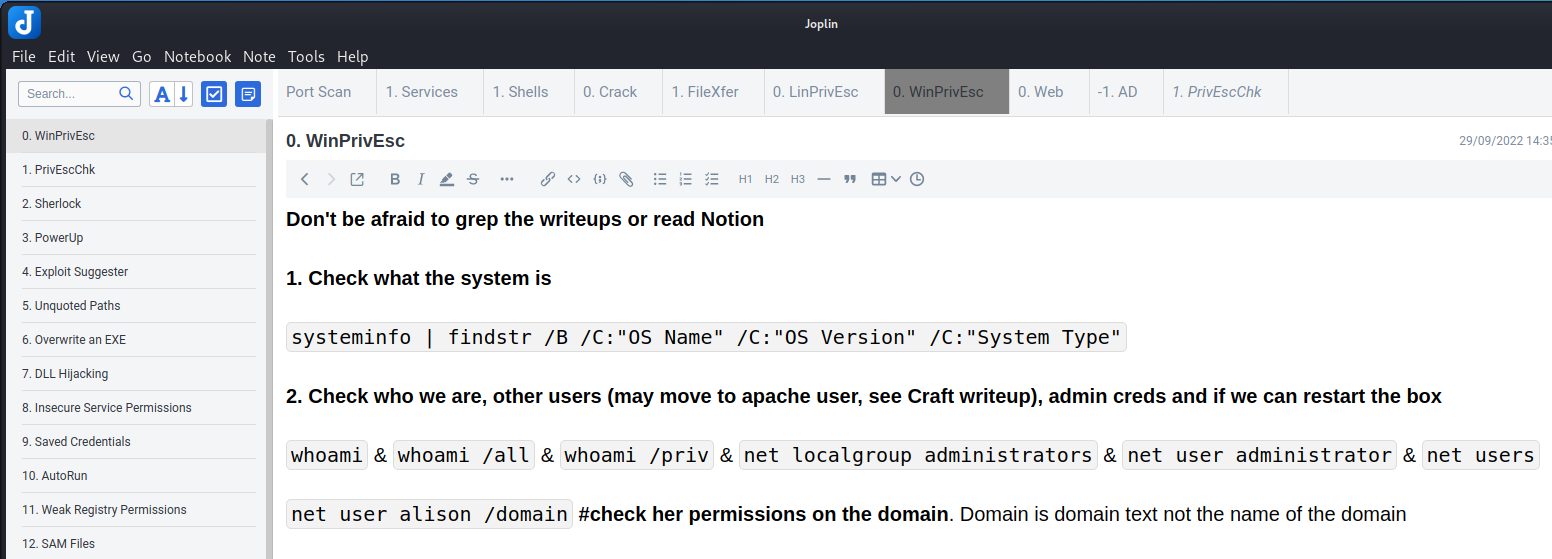
TJ Null recommended Joplin and his Joplin (jex) notes are also here:
https://github.com/tjnull/TJ-JPT/blob/master/TJ-Pentest-Template-2.0.jex
I used Notion for storing one big table of all the boxes I had cracked with 2 or 3 lines on what to look out for or mistakes I made which I called ‘Lessons Learned’.
I also set up an AD lab at home which was good fun and worth the effort to get more experience.
I saved all the Writeups I got from various sources too which I could grep if needs be during the exam although I didn’t need to. I did reread them before the exam though.
The excercise checklist I created may no longer be necessary since the move to topic exercises but these Bash scripts used with Autorecon might still come in useful especially the netcat one to connect to open ports and return the result.
https://github.com/Cyb3rC3lt/OSCP-Exercise-Checklist
https://github.com/Cyb3rC3lt/OSCP-Bash-Scripts
Final thoughts
Overall the process has been enjoyable although the exam really is a tough physical and mental test to get through but maybe that what provides the value to recruiters. The pdf exercises are no longer a thing which is a good move by Offsec because that part off the course wasn’t fun at all and it is now good to know you have the 10% before you go into the exam. I must thank Offsec for including AD in the exam as that turned out to be the aspect I enjoyed most and Red teaming is now my long term goal.
I think the most rewarding part of the process is the people and I am talking to a lot of the readers of this post. Without fail people have been very encouraging and helpful throughout the process. From Reddit posters who you may PM directly for info or students\admins on the Discord who get in touch and Offsec themselves for running the Friday catch up sessions and other things. I even had a senior manager from Offsec contact me one Friday night just to ask how I was getting on which was very nice. The students and mentors in Cyber Security are the real winners in this story.