10 May 2023
Update: These 3 modules are now live on the CrackMapExec repository.
Recently I have been dabbling in some CrackMapExec(CME) module development so I thought it would be good to create a post on it. For those of you who have never heard of this tool, which would probably be a rarity in the Cyber Security world, it is aptly described as: ‘A swiss army knife for pentesting networks’.
It is one of the goto tools for any internal pen tests and comes with many user generated modules. These range from basic checks like if LDAP signing is enabled, to advanced things like running Mimikatz remotely, so it covers a lot of bases.
During some recent pentests I have been wanting to impersonate ‘Domain Admins’ at times and I wanted to be able to quickly look up who they were. So rather than go to the trouble of starting up BloodHound, running ldapdomaindump or crafting a LDAP search filter I thought “wouldn’t it be great if CME could do it”.
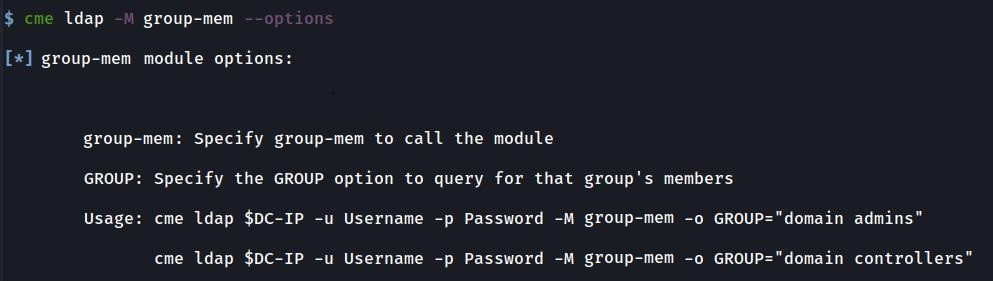
It has modules for returning the users and groups, but not for informing us of what users belong to what groups. This is where the idea for the module named GROUP-MEM came about which is just shorthand for ‘group membership’.
The thinking around my second module was that at times I like to be able to figure out what are the names and IPs of the servers in the domain. Sometimes we aren’t interested in seeing a list of tens of Windows 10 workstations that CME may return, but just a limited subset for us to plan our attack around such has servers or DCs.
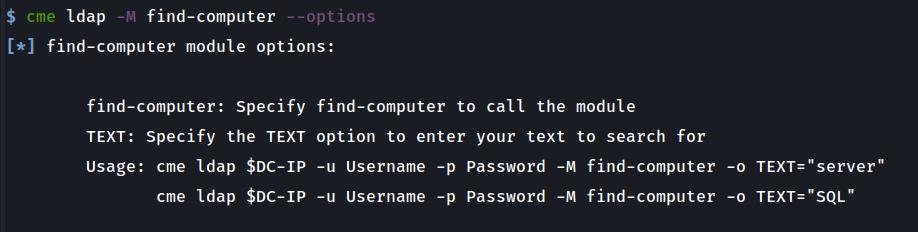
This is where the idea for the second module named FIND-COMPUTER originated. It uses LDAP to look up all the computer objects with the ‘operating system’ description or name matching the string you provide it and returns the list of computers and their IPs. One thing to note is that if there are computer accounts in LDAP that are only objects and not ‘live’, no IP will be returned, so it isn’t scanning the network but looking up objects.
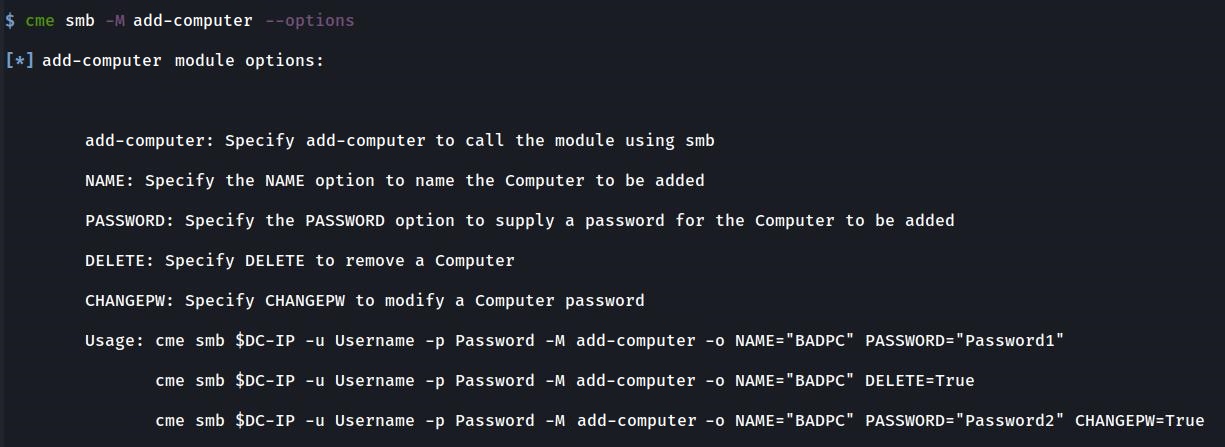
Finally I really like the addcomputer.py script from impacket so I wanted to port that over to CME which became my ADD-COMPUTER module.
Installation
Update: Now just checkout the latest CME code so no need to manually install them.
They can be downloaded here. Then place them here: ~/.cme/modules
GROUP-MEM, FIND-COMPUTER and ADD-COMPUTER Modules
To run them is very easy:
GROUP-MEM Module: Returning Domain Admins
crackmapexec ldap $DC_IP -u Username -p Password -M GROUP-MEM -o GROUP="domain admins"GROUP-MEM Module: Returning Domain Controllers
crackmapexec ldap $DC_IP -u Username -p Password -M GROUP-MEM -o GROUP="domain controllers"FIND-COMPUTER Module: Returning Computers with ‘server’ in their description or name
crackmapexec ldap $DC_IP -u Username -p Password -M FIND-COMPUTER -o TEXT="server"ADD-COMPUTER Module: Adding a new computer
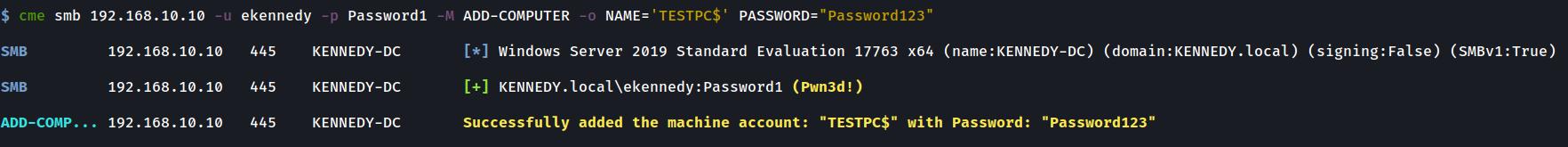
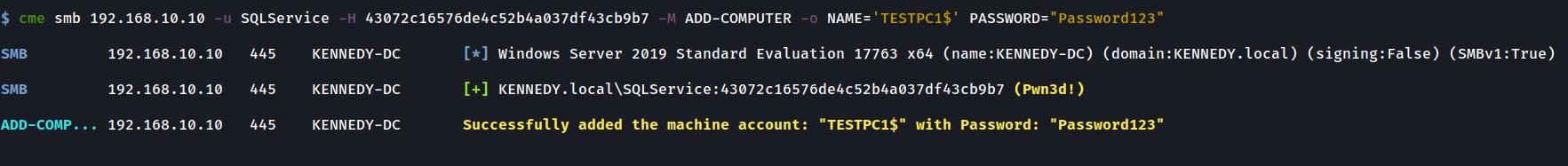
crackmapexec smb $DC_IP -u Username -p Password -M ADD-COMPUTER -o NAME="BADPC1001" PASSWORD="Password1?"ADD-COMPUTER Module: Adding a new computer via Kerberos
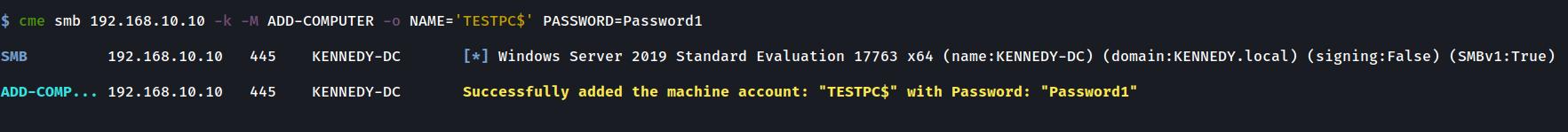
crackmapexec smb $DC_IP -k -M ADD-COMPUTER -o NAME="BADPC1001" PASSWORD="Password1?"ADD-COMPUTER Module: Changing a Computer password
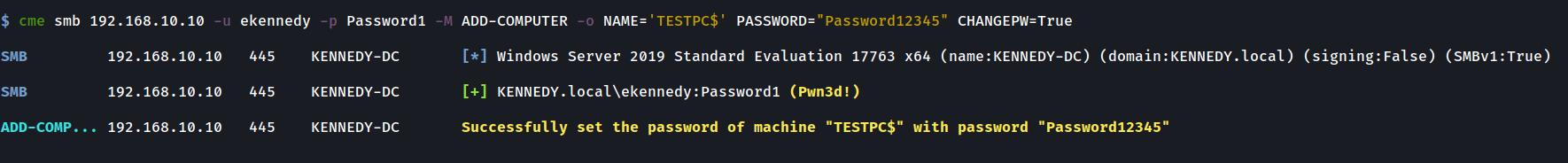
crackmapexec smb $DC_IP -u Username -p Password -M ADD-COMPUTER -o NAME="BADPC1001" PASSWORD="Password1?" CHANGEPW=TRUEADD-COMPUTER Module: Deleting a Computer
crackmapexec smb $DC_IP -u Username -p Password -M ADD-COMPUTER -o NAME="BADPC1001" DELETE=TRUETheir usage is also visible via the command line
GROUP-MEM Results
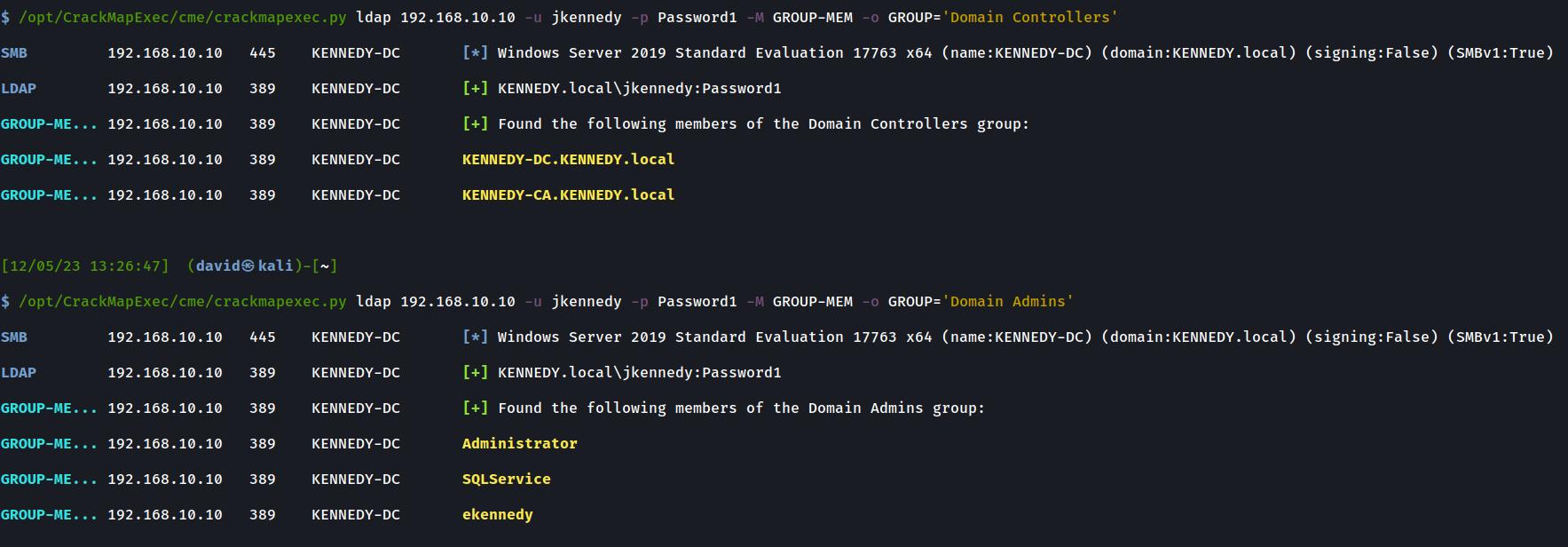
Here are some examples of the output from the GROUP-MEM module shown below:
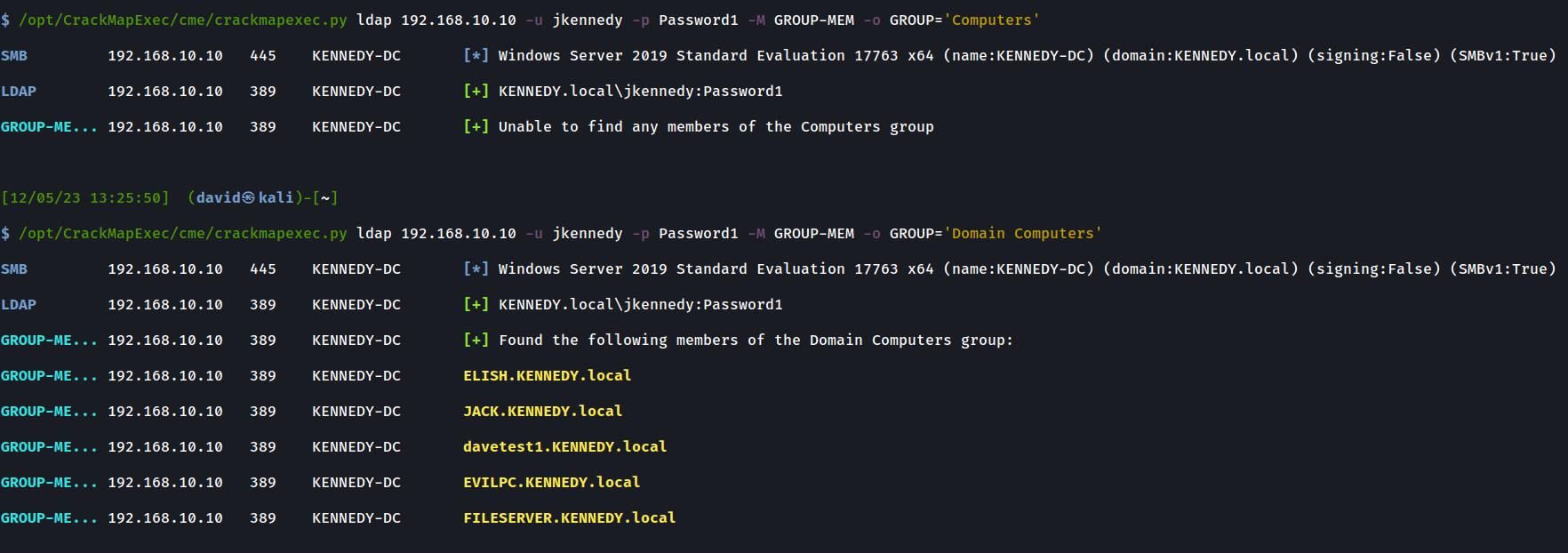
Returning Domain Computers
This example illustrates specifying an incorrect group name ‘Computers’ and the subsequent error handling in place to manage this.
Then it shows the output of when a correct ‘Computers’ group named ‘Domain Computers’ is specified.
Here you can also easily verify if any RBCD machines such as the EVILPC shown below was successfully added or not during your testing.
Returning Domain Controllers and Domain Admins
FIND-COMPUTER Results
Here are some examples of the output from the FIND-COMPUTER module shown below:
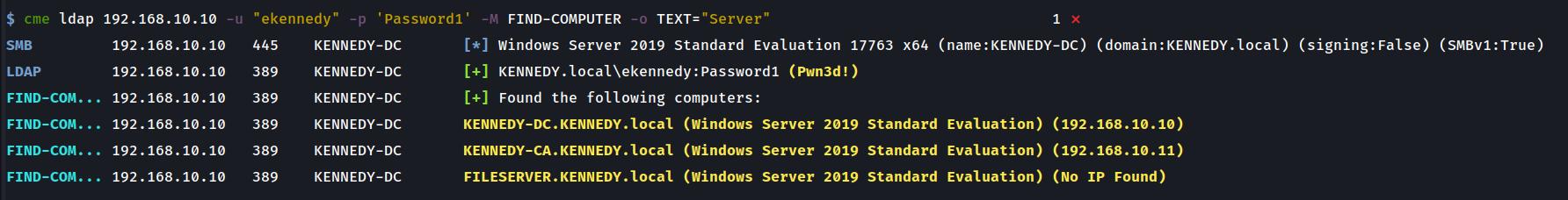
Returning Servers matching the supplied text
This example returns computers with ‘server’ in their name or operating system
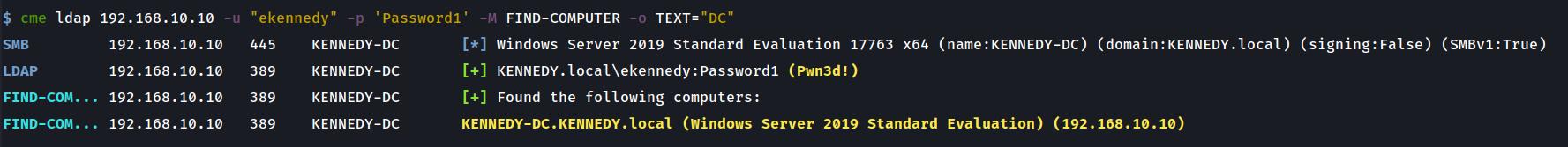
Returning computers with ‘DC’ in their name or operating system
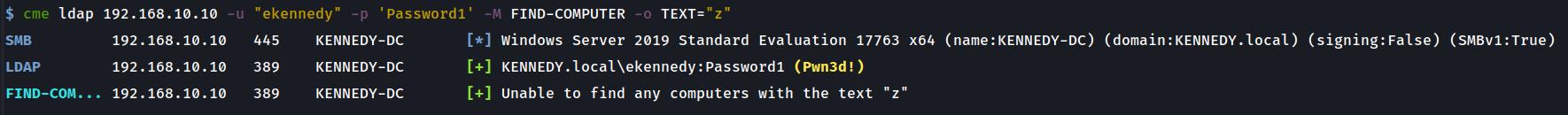
Returning a failed server lookup which illustrates its error handling
This example shows a scenario of a ‘Computer’ object described with the text ‘z’ which is unable to be found.
ADD-COMPUTER Results
Here are some examples of the output from the ADD-COMPUTER module shown below:
Adding a Computer with credentials, hashes or using Kerberos
Changing a Computer password
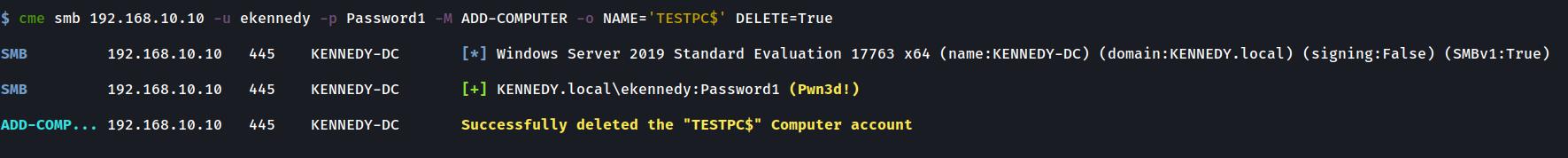
Deleting a Computer
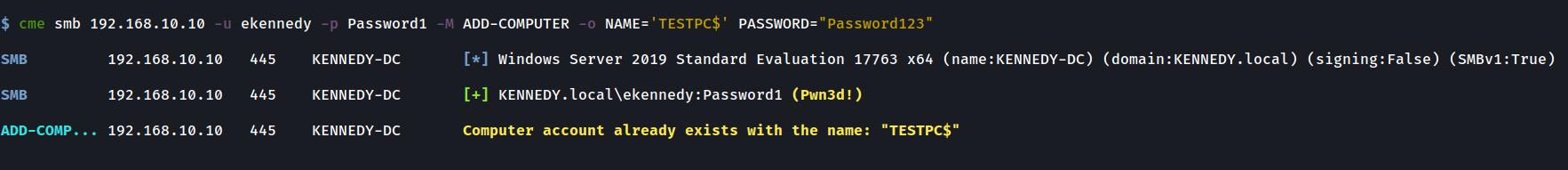
Error handling if a Computer already exists with that name
Final Thoughts
It’s been really fun learning Python over the past few weeks especially with the culmination of producing some handy tools. I have successfully used these on a Pentest recently and I did feel they were quite useful so feel free to download them and try them out. Enjoy!