20 Feb 2023
Although not strictly using Red Teaming techniques I thought posting this may be of interest to some people. Recently I undertook my first internal pentest and I manged to abuse a misconfiguration in Active Directory Certificate Services which gave me ‘Domain Admin’ privileges.
Below is a bit of background on the vulnerability and how I went about it.
What are Active Directory Certificate Services?
Active Directory Certificate Services or AD CS for short allows companies to provide an on-site Public / Infrastructure (PKI) so it can generate, check and revoke public key certificates. In turn, these certificates have various uses including encryption of network traffic, files and emails.
This infrastructure is normally hosted on a separate Windows Server hosting the ‘Certificate Authority’ (of which there can be more than one) and is responsible for managing the on-site certificates. Overall, the infrastructure is made up of 6 components:
- Certification Authorities – these manage certificate validation and issue certs.
- CA Web enrolment – this connects users to a Certificate Authority via a Web Browser
- Certificate Enrolment Policy Web Service – this allows computers and users to query their enrolment rights
- Certificate Enrolment Web Service – this allows computers and users to enrol certificates
- Network Device Enrolment Service – this lets network devices without domain accounts retrieve certificates
- Online Responder – this responds to requests about a certificate’s status
AD CS Vulnerabilities
Back in 2021, Will Schroeder (@harmj0y) from SpecterOps released a research white paper entitled “Certified Pre-Owned: Abusing Active Directory Certificate Services” which caused quite a stir in the offensive and defensive security world. It became obvious that a whole new avenue of attacks had opened up for would-be attackers due to consistent misconfiguration in AD CS by many companies.
They classified each attack vector with the prefix ESC of which there are 8 in the original white paper. The 8 attack vectors can lead to lots of avenues of attack which they highlighted in this quote from their whitepaper:
“AD CS is widely deployed, and provides attackers opportunities for credential theft, machine persistence, domain escalation, and subtle domain persistence.”
For this blog post, I will focus on ESC8 which I had some recent success in exploiting which led to a complete Domain takeover.
ESC8 Abuse
ESC8 can be abused because some enrolment HTTP endpoints do not have HTTPS enabled and in general AD CS rarely has NTLM relay protections enabled by default. What this means is the Certificate Authority’s enrolment page pictured below can be passed data from another server within the network and it will not check that the data is coming straight from that specific server or if the data has instead been passed (relayed) by an attacker.
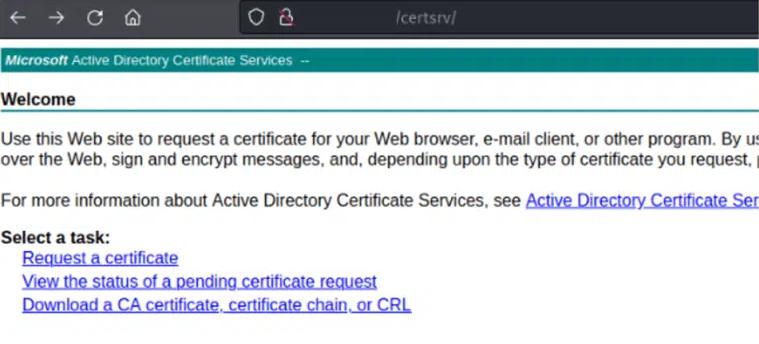
This opens up an avenue of attack for a threat actor (in this case me) to exploit. A full abuse sequence of ESC8 is pictured below. Keep in mind the Certificate Authority on the right contains the webpage pictured above that we want to relay the ‘Target’ authentication to, but it won’t verify it is actually the Target doing so.
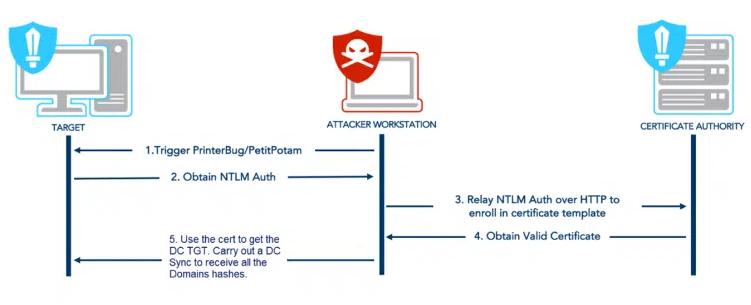
ESC8 Abuse Sequence
The sequence of attack is as follows:
- The Attacker (Kali Linux in our case) uses a bug known as ‘PetitPotam’ which makes an RPC call to our Target, which in our case was the Domain Controller, which tricks the Target to authenticate back to our Attacker machine.
- Our Attacker machine then receives the Target authentication and instead of storing it immediately passes it on to the vulnerable website at the Certificate Authority.
- The Certificate Authority then thinks that we are the Target and responds to us as if we are the Target.
- The response, in this case, is that the CA sends a valid Certificate intended for the Target, but instead to us.
- We then take the Target certificate and convert it to a TGT, which is essentially like a machine’s credentials. Now that we have the Target’s TGT, we have now become for all intents and purposes (or at least authentication-based ones!) the Target machine. Given the Target is a Domain Controller, which is the most powerful machine on the network, we can run from our Kali machine the DC Sync process which Domain Controllers run to keep in sync with other Domain Controllers. This sync process provides us with every username/password hash in the whole domain so we can log in as the Administrator.
At this point, we can add our test user to the ‘Domain Admins’ as an ‘Indication of Compromise’ (IOC).
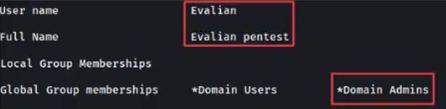
As I see daily, the next step for groups who use Ransomware would be to encrypt all of the data on the domain so we can see how dangerous this type of attack can become.
Remediation
- Organisations should disable these HTTP-based enrolment server roles if they are not in use.
- Disable NTLM authentication using GPOs or configure the associated IIS applications to only accept Kerberos authentication.
- If organisations cannot remove the endpoints or outright disable NTLM authentication, they should only allow HTTPS traffic and configure the IIS applications to use Extended Protection for Authentication.
- Further remediation detail: Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)
Conclusion
Active Directory is used by tens of thousands of companies including 90 per cent of the Fortune 1000 companies. The majority of these will likely use Active Directory Certificate Services meaning that attackers could have rich pickings if AD CS has not been securely configured.